G’day everyone! Hope you’re all well. Quick one today that I know will resonate with anyone managing Azure Virtual Desktop (AVD) or Windows 365 environments – those bloody annoying Microsoft Teams privacy prompts!
You know the ones I’m talking about. Every time a new user logs into their AVD session or Windows 365 Cloud PC, they get hit with “Let Microsoft Teams access your microphone?” and “Let Microsoft Teams VDI Optimizer access your microphone?” popups. Users either click “No” out of confusion (breaking their Teams experience in virtual desktop environments) or you get support tickets asking what they should do.
I’ve been working on a solution to automatically grant these Teams privacy settings on users’ behalf via Microsoft Intune policies, so they get the optimal Teams experience from day one without any annoying camera and microphone prompts. Turns out there are actually two sets of Intune configurations you need – one for the AVD session hosts and Windows 365 Cloud PCs themselves, and another for the end-user devices (your thin clients) running the Windows App for Azure Virtual Desktop.
Let me show you how to configure these Teams privacy policies properly using Microsoft Intune and give your virtual desktop users a seamless Teams experience from their first login to Azure Virtual Desktop and Windows 365.
The Problem: Privacy Prompt Hell for Virtual Desktop Users
Right, so here’s what’s happening in your environment. When users first launch Microsoft Teams in their AVD session or Windows 365 Cloud PC, they’re immediately bombarded with privacy consent prompts asking for access to their camera, microphone, and sometimes location services.
The issue is twofold:
First, you get the standard Teams privacy prompt asking “Let Microsoft Teams access your microphone?” Within the AVD Session Host(s) or Cloud PC(s). This appears because Windows needs explicit user consent before allowing applications to access these privacy-sensitive devices.

Second, on your end-user device (thin client maybe), you often get an additional prompt for “Let Microsoft Teams VDI Optimizer access your microphone?” This is because Teams uses the VDI optimization components to ensure proper audio/video redirection between the virtual session and the local client device.

The result? Users are confused and half your users probably click “No” thinking it’s some sort of security risk. Then they wonder why their microphone doesn’t work in Teams meetings and blame the “rubbish virtual desktop setup.”
Even worse, these prompts can appear multiple times – sometimes after Windows updates, profile rebuilds, or when switching between different client devices. It’s a proper pain in the backside for everyone involved.
The Solution: Intune Policy Configuration
The good news is that Microsoft Intune can handle these privacy settings automatically through policy configuration. Instead of relying on users to make the right choice (spoiler: they often don’t), we can pre-configure the privacy permissions they need for a seamless Teams experience.
We need to configure privacy settings in two places – the virtual desktop environment itself (your AVD session hosts or Windows 365 Cloud PCs) and the end-user devices (the thin clients or local machines running Windows App). This dual configuration ensures Teams gets the permissions it needs regardless of how the audio/video redirection is handled.
AVD Host/Cloud PC Side Configuration
Gather the AppX family name
We need to gather the Microsoft Teams Appx package family name, to go this, open PowerShell and then the following or simply copy the below family package name:
Get-AppxPackage -Name *Teams*Which should return the following:

Save this!
Create the AVD Host \ Cloud PC Intune profile
Within Intune, create a new settings catalogue configuration profile:
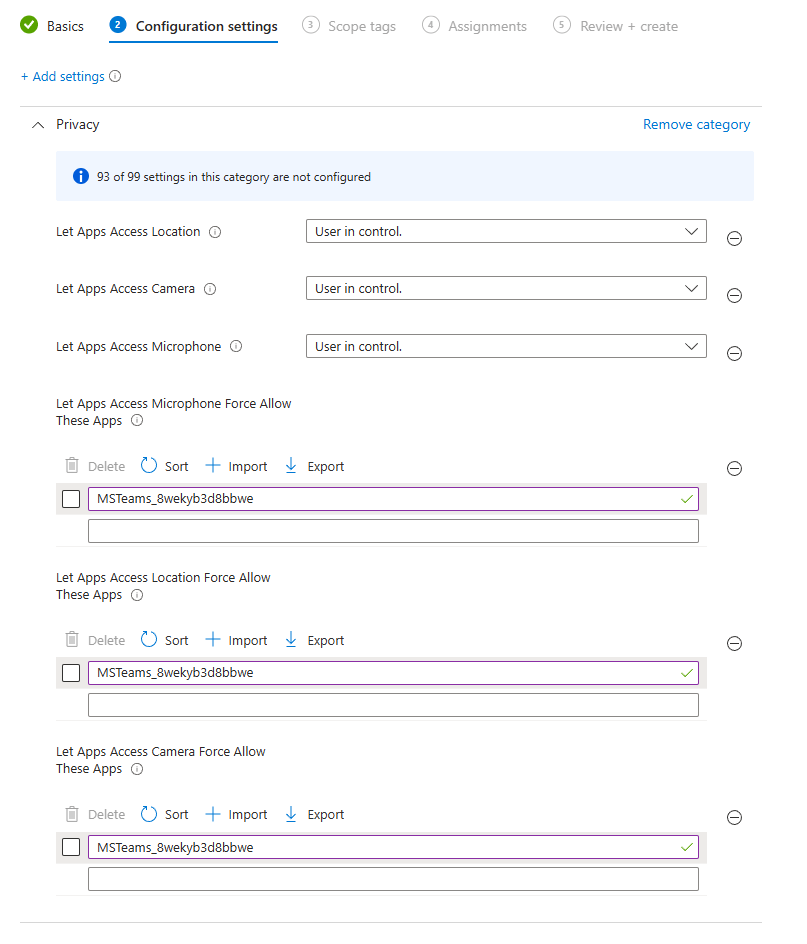
Then within the settings search for Let Apps Access* and then select Privacy, like so:

We want the following:
- Let Apps Access Location
- Let Apps Access Camera
- Let Apps Access Microphone
- Let Apps Access Camera Force Allow These Apps
- Let Apps Access Location Force Allow These Apps
- Let Apps Access Microphone Force Allow These Apps
Under each one add in the MS Teams family package name, ending up like so:
💡 Why Set the Master Microphone/Camera/Location Policy?
You might wonder why we set the main “Let Apps Access Microphone” policy to “User in control” when we’re already specifically force allowing Teams access below.
While the “Force Allow These Apps” policy should theoretically handle everything, setting the master policy ensures the microphone privacy framework is properly enabled before our app-specific rules are applied. Some Windows builds can be unpredictable about applying granular app permissions if the master privacy control is set to “Force deny.”
It’s essentially enabling the underlying privacy system before applying specific app exceptions – just ensures everything works reliably without any odd edge cases!
Now deploy the profile to your AVD Session Hosts and or Cloud PCs. (Note: You can also use these policies on thick clients, too!)
End-User Device Side Configuration
Gather the AppX family name (Again, but slightly different!)
I’m going to assume that you’re using the Windows App to access AVD \ Cloud PCs. For this, we need to gather a slightly different Appx family name, this is for the slimcore ‘Microsoft Teams VDI Optimizer’, which does as the name suggests.
On your client devices, run the following PowerShell or simply copy the below family package name:
Get-AppxPackage Microsoft.Teams.SlimCore*And you’ll want the vdihost* family package name, like so:

Again, save this for later!
Create the End-User Intune profile
Within Intune, create a new settings catalogue profile:

As before, add in the same settings but this time change the family package name to the above, like so:

Assign to your end-user devices, where applicable. Thats it!
Trust but Verify
How do we know this worked? Well, for one, hopefully users won’t receive prompts when launching Teams via the Windows App, but also, you can check the following location within the settings app:
AVD Host \ Cloud PC:

End-User Device:



How would we do it for non-managed endpoints not controlled by Intune.
I have it set on GPO side
Hi Rikesh,
Unless you have some kind of management on the devices then there’s nothing you can do other than add to your user comms to ensure that users accept the prompt(s) and \ or go into app settings and ensure that all three tickboxes are enabled (see last screenshot on post for what I’m referring to).
Thanks,
Alex.